- Software - Simulation
- Software
- Test software
- MER Systems Ltd

- Products
- Catalogs
- News & Trends
- Exhibitions
Management software SeMScontroltestmeasurement
Add to favorites
Compare this product
fo_shop_gate_exact_title
Characteristics
- Function
- management, control, test, measurement, security, calculation, for maintenance
- Applications
- for aeronautics, for airport
- Deployment mode
- web-based
Description
Comprehensive security management solution in compliance with ICAO Annex 17 and Doc 8973 - Aviation Security Manual.
MAIN FEATURES
Threat landscape (Threat sources & agents identification and assessment)
Asset landscape (Critical asset classification and identification)
Loss landscape (Impact and outcomes classification)
Control landscape (Preventive and recovery controls)
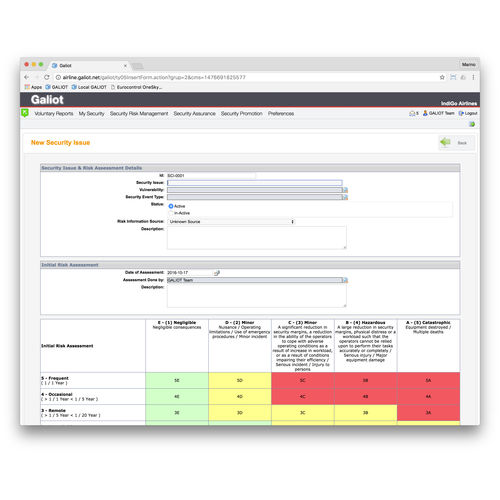
Vulnerabilities identification and assessment
Multiple security scenarios risk assessment
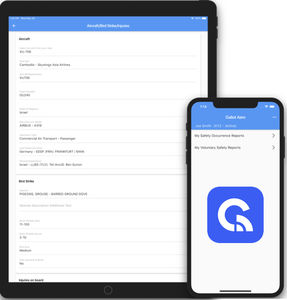
Voluntary and security occurrence reporting
Security incident investigation
Root cause investigation methodology
Security controls efficiency and reliability calculation
Security test and inspection
Corrective actions management
Security Assurance and Staff Permits Management
Security performance measurement and monitoring
Security promotion
WHAT MAKES GALIOT SeMS DIFFERENT?
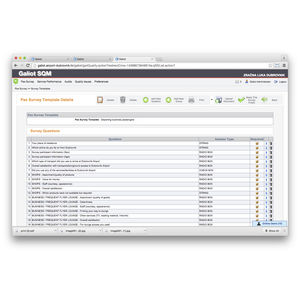
Dedicated security audit and security survey management
Integrated with security equipment maintenance & failure reporting (GALIOT MMS)
SMS, ISO/IEC 27005 and FAIR best practices included
Plan, Do, Check, Act management system
Risk-based security management
Risk assessment approval and re-assessment policy
Four Days Hands on Security Workshop
Risk Assessment as a function of threat probability, vulnerability exposure and asset Criticality, i.e. Risk = f (T, V, A)
Bow-Tie risk assessment methodology integrated with semi-quantitative mathematical model based on R=f(T,V,A) equitation for best/worse risk scenario calculation.
Internal push notification and reporting engine (email and/or text message)
Security control based investigation (B-SCAT investigation method)
*Prices are pre-tax. They exclude delivery charges and customs duties and do not include additional charges for installation or activation options. Prices are indicative only and may vary by country, with changes to the cost of raw materials and exchange rates.